
Face-INT
Protecting your biometric data
179% of funding target
Highlights
Highlights
A true breakthrough for the field of biometric face recognition
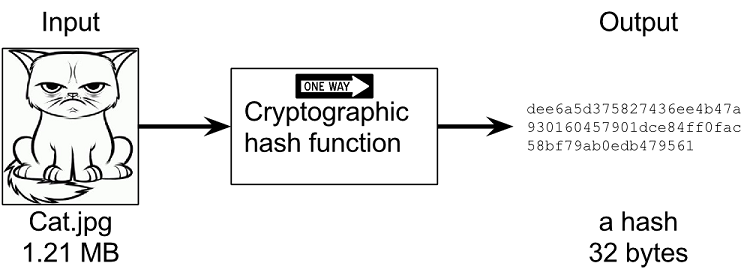
The main issue preventing existing face recognition technologies from becoming a common biometric standard is the need to retain and keep user data, for the purpose of authentication. And therefore do not comply with existing regulatory demands worldwide, which require user consent in order to store sensitive data. Face-INT has developed a unique encryption algorithm, which allows for the first time an identification process without the need to save any biometric data. The algorithm uses a hash-type function to turn the user’s image into a long, encrypted sequence of numbers and symbols, from which the original biometric information cannot be recovered in any way (in a process known as One-Way Encryption).
A solution for the "bottleneck" of the Next Generation Biometrics market
The Next Generation Biometrics related-markets, in which Face-INT operates, are growing at an extremely rapid annual rate, and according to analysts' forecasts are expected to reach tens of billions of dollars by 2023. The company's innovative and unique solution will enable the use of biometric data in the safest manner, while fully complying with the required international standards (FIDO2, GDPR) and without storing any data - solving a major technological barrier, answering a deep need and naturally integrating into this market, which has nearly infinite potential - both in terms of possible uses and applications, as well as a vast supply of relevant business sectors.
Attractive IP, patents in registration in Israel and worldwide
Face-INT has completed the filing of the patent application In Israel, in an accelerated process (Application No. 278342) which also allows the company to register the patent in 150 additional countries, in accordance with the PCT Convention. In the US, the company has filed an application for Provisional US Patent (No. US62879436), and is currently working on a patent to protect further developments, which will be added to the company's unique IP, making it an attractive target for investment, merger or acquisition.
 |
A signed sales contract with one of Israel's leading property-management firms
After a successful pilot conducted at the "Sea View" building in Herzliya, in which the Face-INT system was installed at the various entrances to the business complex, the company signed an agreement to sell the systems installed in the building to Natam, one of the largest property management companies in Israel. The company is currently in negotiations to sign additional contracts for the installation of the system in other buildings, also managed by Natam.

Investing in a finished product, following a successful pilot, with existing sales activity
Sentech (which has merged with Next Gen), has already purchased Face-INT's system for an experiment conducted at Assaf Harofeh hospital, testing devices for quick corona detection, in which experimenters identified through a dedicated face-recognition-based app. This pilot was completed with great success and later on, the client intends to use the technology also at international border crossings worldwide, a use for which Face-INT's tech was chosen due to its great sensitivity regarding biometric data security. Another pilot was successfully completed in collaboration with “Beit HaLohem”, a chain of sports centers with thousands of subscribers, for the purpose of an identification system that will replace the old fashioned subscription cards.

Pitch
Pitch
The Need
What was once considered science fiction, has in many cases become a reality over the years: from automatically opening sliding doors to touchscreen tablets, invention sometimes leaps from the page into reality. This is also true for the field of biometrics and facial recognition technologies - on one hand, a super-advanced and convenient high-tech tool for the identification for users, but at the same time - a tool that might be abused and used for malicious purposes, from stealing sensitive data, to taking over someone's entire identity.
In the ultra-modern technological age we live in, each of us is required to identify daily, whether online (on banking, insurance, credit card, health services sites and more), or physically - at work, the gym, the airport, and sometimes even at the entrance to our own home.
In fact, on a global scale, according to estimates, this outdated and mandatory use of id cards and passwords consumes about 1,300 years of cumulative human life (!). And if that wasn’t enough, any such identification procedure is also a wide open backdoor which may be prone to phishing attempts (in which fictitious websites impersonate reputable services, and try to steal the user’s login credentials, credit data or passwords).
Despite the speed, elegance and convenience built into the very concept of face recognition technologies, which are based on a way of identification that can not be forgotten or lost, saving the need for technical support whenever a password is forgotten, these systems haven't managed yet to become a real substitute for personal identification needs, mainly because of the issue of users' privacy and related strict regulatory requirements - companies are not allowed to keep sensitive personal data, which a third party could potentially decipher.
Another market desperate to solve this inherent issue is the rapidly evolving field of IoT (Internet of Things), which includes a vast variety of "smart" devices, many of which require a user identification procedure to operate, or exit "lock" mode, where face recognition tech can efficiently replace many items such as car keys, house keys, various coders and more.
The Solution
In a truly innovative breakthrough for the field of biometric face recognition, Face-INT has developed a unique encryption algorithm, which enables - for the first time - biometric identification without storing any data, saving the need to keep or secure the inherently sensitive biometric info, in accordance with global regulatory requirements.
The company's patented solution actually turns this biometric data, using a hash function, into a very long string of numbers, from which the original data cannot be recovered in any way.
Customers using Face-INT's technology can, following a short registration process via mobile phone, identify themselves easily and quickly, at any time, using only their face.
How does it work?
In addition, the Face-INT system can continue to identify users even when their outer appearance changes slightly, thanks to the use of advanced ML (machine learning) components, and knows how to "bridge" over changes such as growing a new beard, wearing glasses, etc., and even has the ability to overcome possible spoofing attempts.
Technology
To fully understand the uniqueness of Face-INT's technology, keep in mind that every face recognition system has an engine, whose function is to process each face image and output it as a set of values ??(face descriptors), which reflect and characterize the same person - mathematically speaking. For the sake of abstraction, let's say each value expresses some important feature - for example, the size of each organ, the distance between the eyes, the distance between the ears and nose, etc.
In order to identify people in the system, the same values ??must be saved initially, at the registration stage, and a mathematical function comparing the set of values ??at the entry stage must be activated, for each of the sets stored in the system - from the registration stage, until the most identical set is found.
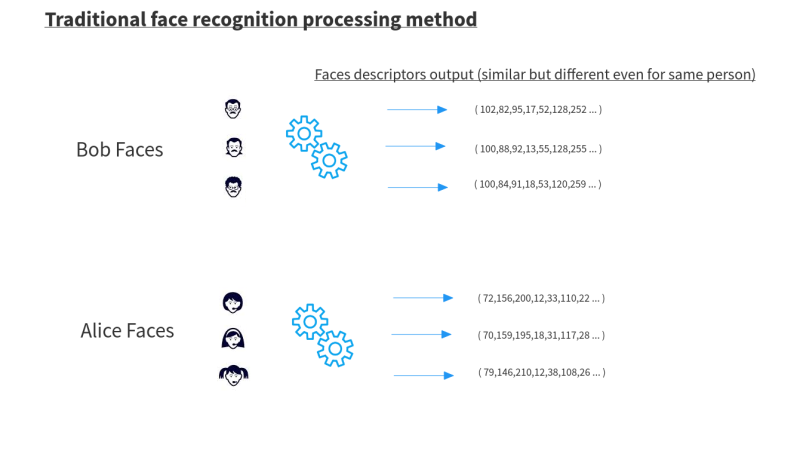
But these face recognition engines can not accurately reproduce the same values ??for the same person every time, since any slight change in the camera conditions (such as angle, lighting, facial expressions), and even more so the changes in a person's appearance over time (hair or makeup, glasses, beard, etc) - cause the data itself to change.
Despite the different results, the function which compares the data sets produces a result of a relatively small "gap" between different images of the same person, and a high difference between images of different people. Based on this figure the system can provide the correct identification outcome.
The main problem with previous face recognition systems, as mentioned, is that the storage of those sets of values in a database, constitutes a barrier in terms of existing regulatory demands around the world, aimed at protecting user privacy.
Standard face recognition system - illustration diagram
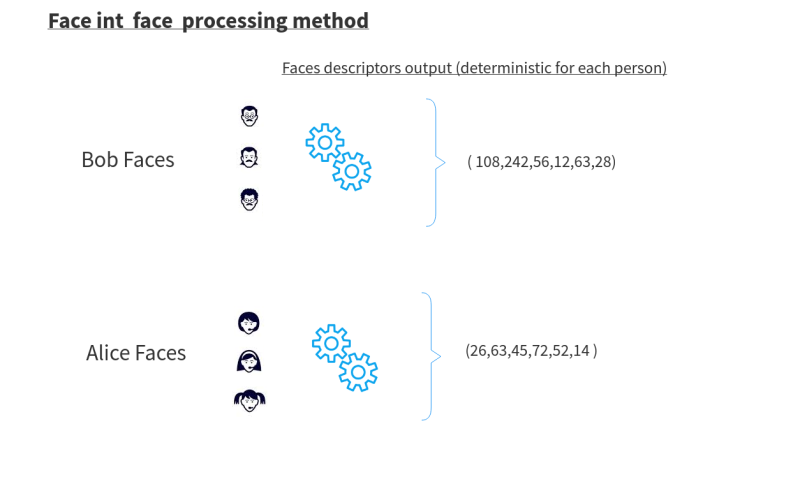
Unlike the standard process, using Face-INT's method, the algorithm is able to produce a fixed set of values for each image of the same person, and learns to ignore different camera conditions as well as any natural changes in the person's appearance over time.
Face-INT's technology - illustration diagram:
This unique ability to reproduce the same fixed (deterministic) set of values, for the same person, makes it possible not to have to save any biometric data, through another step - hash encryption.
Unlike standard encryption, which is defined as two-way encryption, where you can encrypt a value and also decrypt it using the same encryption key, hash encryption is defined as a one-way encryption, which means the encrypted value can't be unlocked in any way, making this method the safest and most common method for password storage, in various systems.
The process in the stage of registration:
- Photographing the user - The Face-INT engine produces a fixed set of values
- The set of values is then encrypted via hash
- The values set is stored in the database, meaning even a possible hack into the system will not provide any biometric / personal data usable in any way by hackers

After registration, each time the user logs in, the system performs the following actions:
- Photographing the user - The Face-INT engine produces a fixed set of values again
- The set of values is then encrypted via hash
- The system scans the database and looks for a match for approval
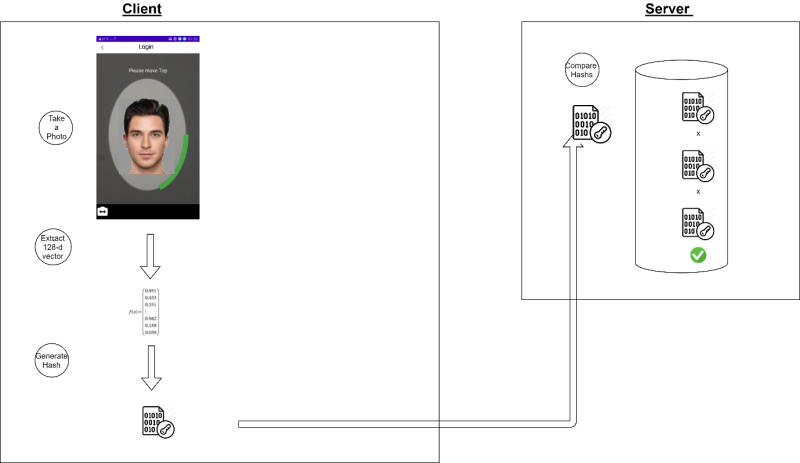
Existing face recognition systems don't currently use hash this way, since Face-INT is the first to develop an algorithm that allows the creation of an encrypted set of values which has the ability to remain identical, even between the registration process and later logins. Without this unique and exclusive development, every single minimal change in the person or camera - produces a completely different encrypted value, making it unusable.
For the purpose of simple password encryption, where the password entered into the system is the same every time, this method is easy and simple to apply, but for complex face recognition where the data obtained is "noisy", other systems simply can not produce a fixed set of values, and therefore of course can not encrypt it in this method, as well.
Team
Team
|
Entrepreneur and experienced manager in the Israeli high-tech industry, founded Gad Line in 1991, which dealt in cable communications. The company employed about 150 employees and was sold in 2000 to the American company COM21. In 2002 Gideon founded SerVision, which developed technology for transmitting video over a cellular network, at a time when the old networks had a bandwidth of merely 10-100 kbps. The company was listed on the AIM Stock Exchange in London and sold many thousands of systems. Face-INT is the third company Gideon has found so far.
|
|
BA in computer science and vast industry experience in projects related to encryption, cryptography, and algorithmics. Noam has led the development at Face-INT from day one, from the concept stage to the existing product.
|
|
BA & MA degrees in engineering from the Technion, an entrepreneur, product manager, and experienced development manager in leading companies in the high-tech industry, including Intel and NDS. He has personally registered 18 patents and established a number of companies, including Smart Link, which had sales of hundreds of millions over six years period, as well as Telesen, Authix Technologies, and more. Has worked as a corporate auditor for the Chief Scientist (now the Innovation Authority), and still serves as a professional patent editor today.
|
|
With extensive experience in the field of face recognition and applied mathematics.
|
|
A full stack developer with six years of experience in the field, serves as the company‘s manager for the DVR field.
|
|
With extensive experience in leading companies towards an IPO as well as raising capital overseas
|
|
An accountant, with a degree in economics and accounting from the Hebrew University, and extensive experience in managing funds in private and public companies.
|






